Cyber SecurityWi-Fi Penetration Testing with Kismet and Wifite: A Checklist for Success
By: Herm Cardona
Introduction
In the dynamic and intricate world of cybersecurity, Wi-Fi penetration testing stands out as a critical task for securing wireless networks. This guide aims to delve deeper into the nuances of Wi-Fi penetration testing, spotlighting essential tools like Kismet and Wi-Fite, and providing a comprehensive checklist for conducting effective and responsible assessments.
Why Wi-Fi Penetration Testing Matters
Wi-Fi networks, while convenient, are often vulnerable to a range of security threats, from weak encryption and poor configuration to sophisticated cyber-attacks. Conducting a thorough Wi-Fi penetration test helps identify and rectify these vulnerabilities, ensuring robust network security.
Comprehensive Stages of Wi-Fi Penetration Testing
1. Reconnaissance – The Art of Information Gathering

Figure 2: Surveying Wireless Networks
Tool Highlight: War-driving with Kismet
Capabilities: Kismet excels in passively collecting packets and detecting hidden networks and clients. Its real power lies in its ability to map the network environment without alerting the target.
Practical Usage: Deploy Kismet to survey the target area. Identify SSIDs, MAC addresses of access points, and types of encryption in use. Pay special attention to any unusual network behaviors or unknown SSIDs that might indicate rogue access points.
War-driving: War-driving is a methodical approach for assessing the security of wireless networks. It involves physically moving through an area – typically in a vehicle, hence the term “driving” – to detect and evaluate the security of wireless networks in that vicinity. Kismet excels in this role (Figure-3).

Figure 3: Kismet – Basic Setup for Wardriving with Kismet
2. Scanning and Enumeration – Unveiling the Network

Figure 4: Enumeration
Kismet for Deeper Insights: Beyond initial reconnaissance, use Kismet to uncover the network structure, identify connected devices, and even pinpoint physical locations of devices using signal strength (Figure-5).
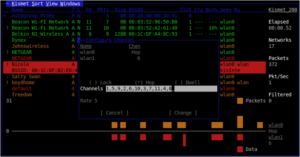
Figure 5: Kismet Detailed Screen
Analyzing Data: This phase is about interpreting the data gathered by Kismet. Look for outdated firmware, weak encryption methods, or excessive data transmission from a particular device.
3. Gaining Access – Cracking the Code

Figure 6: Cracking the Code
Tool Focus: Wifite
Capabilities: Wi-Fite is an automated tool that simplifies the process of cracking WEP, WPA/WPA2, and WPS encrypted networks (Figure-7).
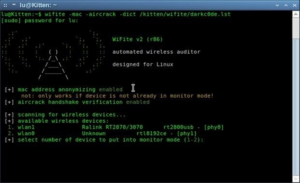
Figure 7: Wifite Automated Wi-Fi Assessment Tool
Execution Strategy: For WPA/WPA2, Wi-Fite can use various methods like evil twin attacks, dictionary attacks, and brute force attacks. Remember, success largely depends on the strength of your word lists and computational power.
4. Maintaining Access and Eavesdropping – The Silent Observer

Figure 8: Sniffing the Network
Beyond Access: Once inside the network, it’s crucial to maintain a low profile. Use tools like Wireshark in tandem with Kismet to monitor network traffic and sniff out sensitive information (Figure-9).
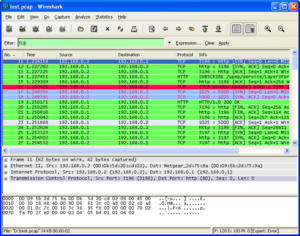
Figure 9: Sniffing with Wireshark
Objective: Look for unencrypted transmissions of sensitive data, such as passwords or personal information, that can be leveraged for further penetration or reported for strengthening network security.
5. Analysis and Reporting – The Finale

Figure 10: Analysis and Reporting Phase
Critical Analysis: This stage involves a thorough analysis of the data collected. Identify patterns, potential security flaws, and areas for improvement.
Reporting: Present your findings in a detailed report, highlighting vulnerabilities, the methods used to exploit them, and recommended actions for remediation.
6. Best Practices and Ethical Considerations

Figure 11: Ethical Hacking and the Law
- Legal Compliance: Ensure you have explicit permission and legal clearance before commencing any penetration test.
- Stay Informed: Keep abreast of the latest developments in Wi-Fi security to refine your testing methods.
- Responsible Reporting: Your report should not just outline vulnerabilities but also provide comprehensive solutions for mitigating these risks.
7. A Deep Dive into Real-World Application
Let’s consider a hypothetical scenario. You’re tasked with testing the Wi-Fi network of a large corporation. You start with Kismet, identifying an array of devices and noticing a few unexpected SSIDs, potentially indicating rogue access points.
Moving to Wi-Fite, you target the WPA2-encrypted employee network. Using a customized dictionary attack, you manage to crack the password, gaining access to the network. Inside, you employ a combination of Kismet and Wireshark to monitor traffic, discovering several unencrypted email transmissions containing confidential information. In your detailed report, you highlight these findings, stressing the need for stronger encryption, better password policies, and increased awareness about secure transmission of sensitive data.
8. Wrapping Up
In conclusion, Wi-Fi penetration testing is a sophisticated and essential aspect of network security. Tools like Kismet and Wi-Fite are invaluable in this process, but they require skilled handling and ethical application. Remember, the ultimate goal is to strengthen the network’s defenses, not just to expose its weaknesses. Stay ethical, stay dedicated, and continue pushing the boundaries of what’s possible in cybersecurity.