Cyber SecurityCross-Site Scripting (XSS) Evasion Techniques: Advanced Methods for Bypassing Modern Security Filters
By: Herm Cardona
Introduction
Cross-Site Scripting (XSS) attacks remain a persistent threat to web application security. As a seasoned expert in cybersecurity and penetration testing, it’s imperative to delve into advanced XSS evasion techniques capable of bypassing modern security filters. Equally important is understanding how developers can effectively mitigate these vulnerabilities. This article explores these advanced evasion strategies, with a detailed focus on encoding techniques among the filter bypass methods. We’ll provide numerous examples and actionable recommendations. Regular penetration testing emerges as a crucial solution to protect against XSS attacks. Don’t wait until it’s too late; schedule your penetration test today!
Understanding the XSS Landscape:
Before we dive into the intricate world of advanced evasion techniques, let’s revisit the foundations of XSS. XSS occurs when malicious scripts are injected into web pages and subsequently executed by unsuspecting users. These scripts can steal sensitive data, manipulate web content, or perform actions on behalf of the victim.

Figure 1: Simple XSS Test
Now, let’s explore advanced XSS evasion techniques that can bypass modern security filters, with a deep dive into encoding methods:
1. Payload Obfuscation:
Attackers often employ payload obfuscation to obscure malicious code from security filters. This entails encoding payloads and using JavaScript tricks. Here’s an example:
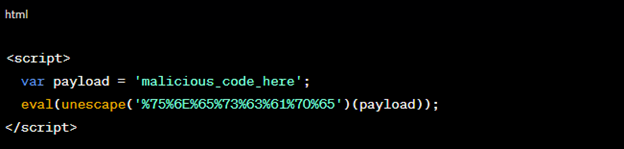
Figure 2: Payload Obfuscation
2. Payload Fragmentation:
Fragmenting payloads into smaller parts and reassembling them on the client-side can evade detection. Attackers can utilize JavaScript functions like `String.fromCharCode()` for this purpose:
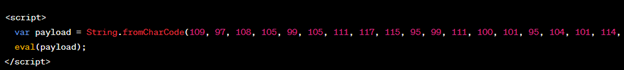
Figure 3: Payload Fragmentation
3. Payload Encoding:
Encoding payloads using techniques like Base64 can thwart security filters. Decoding occurs on the client-side, executing the payload. An example:
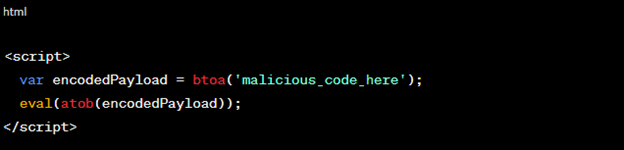
Figure 4: Payload Encoding
Encoding can also be achieved using HTML entities, making it challenging for filters to identify:
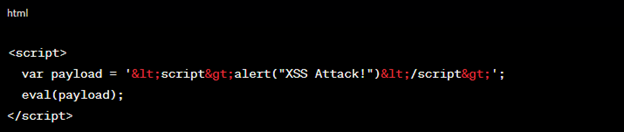
Figure 5: Using HTML Entities
4. Double Encoding:
Double encoding involves encoding the payload multiple times, making it even harder to detect. An example:
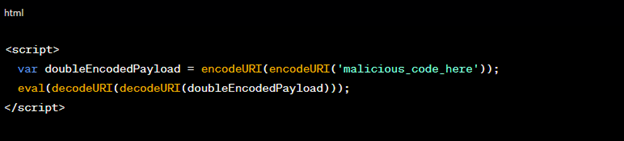
Figure 6: Double Encoding
Mitigation and Prevention:
Developers play a crucial role in mitigating XSS vulnerabilities:
- Input Validation: Implement strict input validation to sanitize user input and reject any malicious content.
- Output Encoding: Encode output data to ensure that user-generated content is treated as data, not executable code.
- Content Security Policy (CSP): Enforce CSP headers to restrict the sources from which content can be loaded.
- Regular Penetration Testing: Schedule periodic penetration tests to proactively identify and remediate vulnerabilities.
Conclusion
Understanding advanced XSS evasion techniques, including encoding methods, is pivotal for cybersecurity professionals and developers alike. With this knowledge, you can assess web applications comprehensively and fortify them against potential threats. Regular penetration testing is a critical solution to identify and rectify XSS vulnerabilities.
Don’t wait until a security breach occurs. Schedule your penetration test today and safeguard your applications from XSS and other emerging threats. Staying vigilant and proactive is the key to security. Stay secure, stay ahead!