Cyber SecurityThe Art of Social Engineering: A Key Tool in Penetration Testing
By: Herm Cardona
Introduction
Social engineering remains one of the most effective techniques in the toolkit of a penetration tester. It exploits the human element, often considered the “weakest link” in the security chain. With the rise of increasingly sophisticated technology solutions, there has never been a better time to refocus on social engineering as a critical component of your security strategy.
What is Social Engineering?
In the realm of cybersecurity, social engineering refers to the psychological manipulation of individuals into divulging confidential information or performing specific actions that compromise security. Examples include phishing emails, pretexting, baiting, and tailgating.
In the field of web application penetration testing, these techniques could be used to manipulate an employee into revealing credentials that could compromise the application’s backend. This is why having secure code is just as crucial as training your staff on recognizing social engineering attempts.
Key Tools for Social Engineering
In the arsenal of a penetration tester, tools like The Social Engineer’s Toolkit (SET) and Cobalt Strike stand out for their efficacy in simulating social engineering attacks. SET, an open-source Python-based toolkit, excels in crafting phishing emails, developing malicious websites, and even generating QR code attacks, serving as an invaluable resource for exploiting human vulnerabilities. Cobalt Strike, while not strictly a social engineering tool, offers advanced capabilities for Adversary Simulations and Red Team Operations, including spear phishing and payload delivery options. Both tools can incorporate JavaScript and PowerShell in their attack vectors. JavaScript can be used to create highly interactive phishing pages for credential harvesting or to exploit browser vulnerabilities. PowerShell, on the other hand, is often utilized in payload delivery and post-exploitation stages, giving attackers the ability to execute scripts and commands on compromised systems. Together, these scripting languages enhance the versatility and effectiveness of social engineering tools, enabling more sophisticated and targeted attacks.
The Social Engineer’s Toolkit (SET)
The Social Engineer’s Toolkit is an open-source framework developed by TrustedSec that focuses on simulating social engineering attacks. Its modules include email phishing campaigns, credential harvesters, and malicious payload delivery, among others.
SET in Action
To give you a taste of how SET works, you could use it to send a phishing email that mimics an internal communication within a company. See a basic example in Figure 1 below:
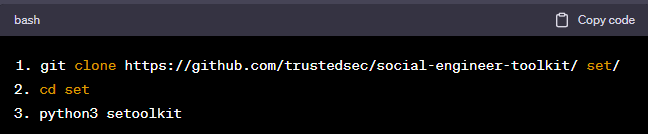
Figure 1: Launching the Social Engineer’s Toolkit
After navigating through the text-based menu to select the email phishing option, you can craft an email with a malicious payload attached or embedded, which then gets sent to the target. A successful phish would result in the target unknowingly executing the malicious payload.
Cobalt Strike
Cobalt Strike is another powerful framework designed for Adversary Simulations and Red Team Operations. While not strictly a social engineering tool, it offers functionalities like spear phishing and payload delivery which can be utilized in social engineering scenarios.
Cobalt Strike for Social Engineering
For instance, Cobalt Strike’s “Beacon” is a payload that can be delivered via a phishing email. Once executed, it gives the attacker a foothold into the network, allowing for lateral movement and further exploitation.
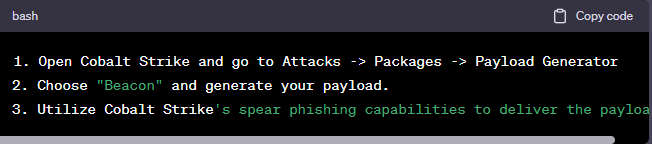
Figure 2: Launching Cobalt Strike
In the context of application security, exploiting a weakness via social engineering can often give you insights into further vulnerabilities within the system. Moreover, JavaScript could be embedded into phishing pages to enhance the chances of credential harvesting, demonstrating its utility even in the sphere of social engineering.
Why You Should Care
Even if you have a solid understanding of Cross-Site Scripting (XSS) and have deployed all necessary server-side security measures, neglecting to educate your team about the risks of social engineering can lead to a breach.
Conclusion
The role of social engineering in penetration testing serves as a potent reminder of the human factor in cybersecurity. Utilizing tools like SET and Cobalt Strike can provide invaluable insights into your organization’s vulnerabilities, allowing for a more robust defense strategy.
Don’t become the next victim of a breach! Schedule your penetration test today!