Cyber SecurityWi-Fi Penetration Testing: War-Driving with Kismet
Unveiling the Invisible: The Role of War-Driving in Wi-Fi Assessments
In the realm of Wi-Fi penetration testing, war-driving remains a pivotal technique. It involves traversing areas to detect and evaluate wireless networks. This approach is vital for pinpointing vulnerabilities, understanding network security configurations, and assessing potential exposure to cyber threats.
Introducing Kismet: The Premier Tool for Network Discovery
Kismet stands out as a network detection, packet sniffing, and intrusion detection system, crucial for war-driving. It operates in a passive mode, collecting detailed information about networks and connected devices, without actively engaging with them.
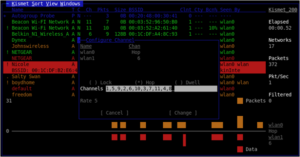
Figure 2: Kismet
Setting Up Kismet for War-Driving: A Comprehensive Guide
1. System Preparation
Ensure your Linux system is updated:
![]()
2. Kismet Installation
Install Kismet:
![]()
3. Configuring Kismet for Alfa AWUS036ACH Antenna
Edit the Kismet configuration file:
![]()
Replace wlanX with your antenna’s interface name, found using iwconfig.
4. Configuring Kismet for BU-353S4 GPS Receiver
Identify your GPS device path:
![]()
Add to kismet.conf:
![]()
5. Launching Kismet
Start Kismet:
![]()
Kismet will begin collecting data using the Alfa antenna and GPS coordinates from the BU-353S4.
6. Data Exporting for Google Maps
Convert Kismet logs to .kml or .kmz for Google Maps using GPSBabel:
![]()
Replace the filename with your actual log file.
7. Visualizing Data on Google Maps

Import the .kml or .kmz file into Google Maps to view your results.
The Alfa AWUS036ACH Antenna and BU-353S4 GPS Receiver in Action
The Alfa AWUS036ACH antenna enhances your ability to detect distant networks, a critical asset in densely networked environments (Figure-3).

Figure 3: Alfa AWUSO36ACH
In conjunction, the BU-353S4 GPS Receiver is indispensable for accurately logging the location of each network, forming the backbone of your geographical analysis (Figure-4).

Figure 4: GPS Receiver
Plotting Your Discoveries: From Data to Maps
The transition from collecting data to visualizing it on Google Maps is a powerful step. It transforms abstract numbers and network names into a tangible map, illustrating the security posture of different areas.
Wrapping Up: The Art of War-Driving with Kismet
War-driving with Kismet, enhanced by the right tools like the Alfa antenna and GPS receiver, offers a comprehensive view of the wireless landscape. Remember, this powerful technique should always be used responsibly and within legal frameworks.

Figure 5: Typical War-driving Setup
As cybersecurity professionals, it’s our duty to understand and illuminate the digital terrain. War-driving with Kismet is more than a technique; it’s a journey into the unseen world of wireless networks, revealing truths critical for securing our digital future. Happy hunting, and may your maps always lead to deeper insights!
Introducing Winmill’s Penetration Testing Stream
War-driving and tools like Kismet reveal the invisible attack surface of Wi-Fi deployments. Winmill’s Penetration Testing Stream takes those findings beyond one-off research: we convert discovery data into prioritized, recurring penetration tests (including wireless assessments), remediation guidance, and continuous validation so organizations can reduce exposure and stay audit-ready. Learn how our subscription model integrates hands-on wireless testing with enterprise reporting and remediation support.
