Cyber SecurityPen Tester’s Notebook – Part 1 – Formatting Nmap Results
By: Herm Cardona
WARNING
- Blog articles related to hacking are only for informational and educational purposes. Any time the word “hacking” is used on this site, it shall be regarded as Ethical Hacking. You may try out these hacks on your own computer at your own risk. Performing hack attempts (without permission) on computers that you do not own is a serious crime under federal law.
- Refer to the laws in your province/country before accessing, using, or in any other way utilizing these materials. These materials are foreducational and research purposes only.
- Any actions and or activities relating to the material contained within this website is solely your responsibility. The misuse of the information in this website can result in criminal charges brought against the persons in question. The author and Winmill Software will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
In this series, Winmill Pentest Engineer Herm Cardona, OSCP, shares professional pen testing tips to help you elevate your ethical hacking skills to the next level. You will learn how professional penetration testers solve some of the most common hurdles encountered during the various phases of real-life ethical hacking engagements.
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts.
Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Nmap CLI results display a tremendous amount of information. In this example we scan host 10.129.1.15 with high verbosity -vv, no name resolution -n, no Ping -Pn, stealth scan -sS, on all ports -p-, and aggressive mode -A. We also specify all output formats with -oA nmap-demo (Figure 1).
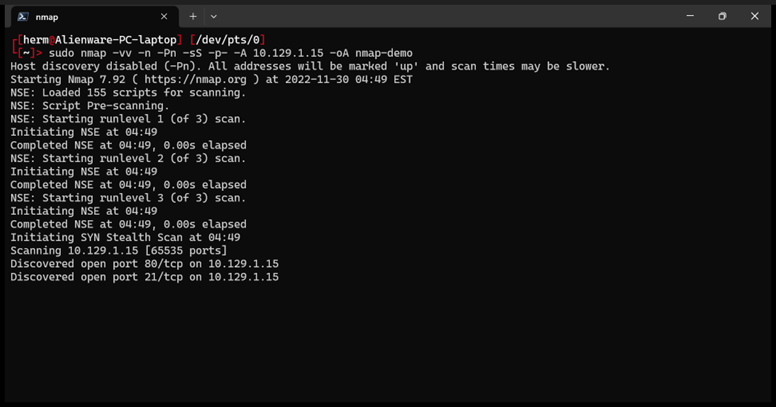
Figure 1: We run an all ports scan on host 10.129.1.15
The oA switch gives us the output in three formats: Greppable Nmap: nmap-demo.gnmap, XML: nmap-demo.xml, and Raw: nmap-demo.nmap. Let’s take a look. First we look at the nmap raw results nmap-demo.nmap (Figure 2).
Figure 2: Raw nmap output.
Next, we look at the greppable output (Figure 3).
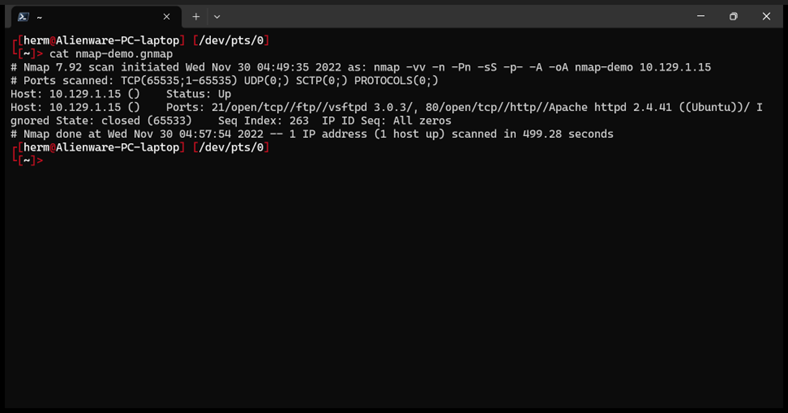
Figure 3: Greppable Output
Finally, we look at the XML Output (Figure 4).
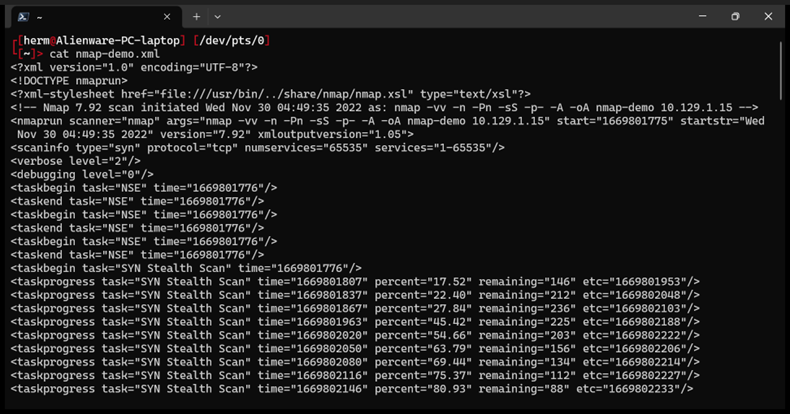
Figure 4: XML Output
While all outputs provide useful information, none of them is truly suitable for displaying as an illustration. Here’s where the “—webxml” flag can help us create a better report. We run the same scan, but this time we add the “—webxml” flag (Figure 5).
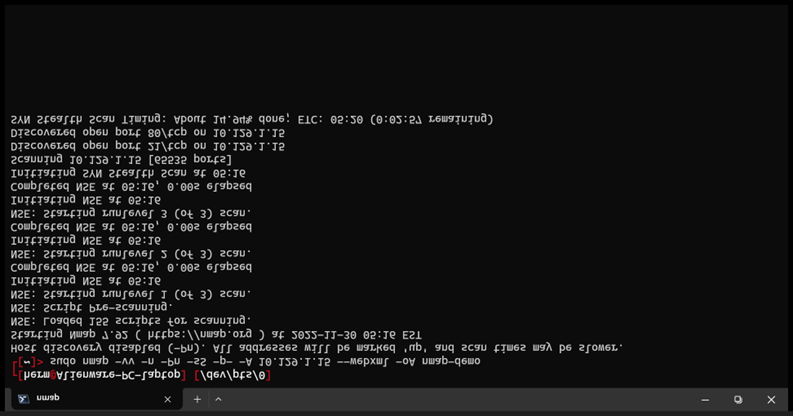
Figure 5: We add the –webxml flag before the -oA switch
We look again at the .xml output, but this time we use our Firefox browser to look at the file with “firefox nmap-demo.xml”. This time we are presented with a nicely formatted scan report (Figure 6).
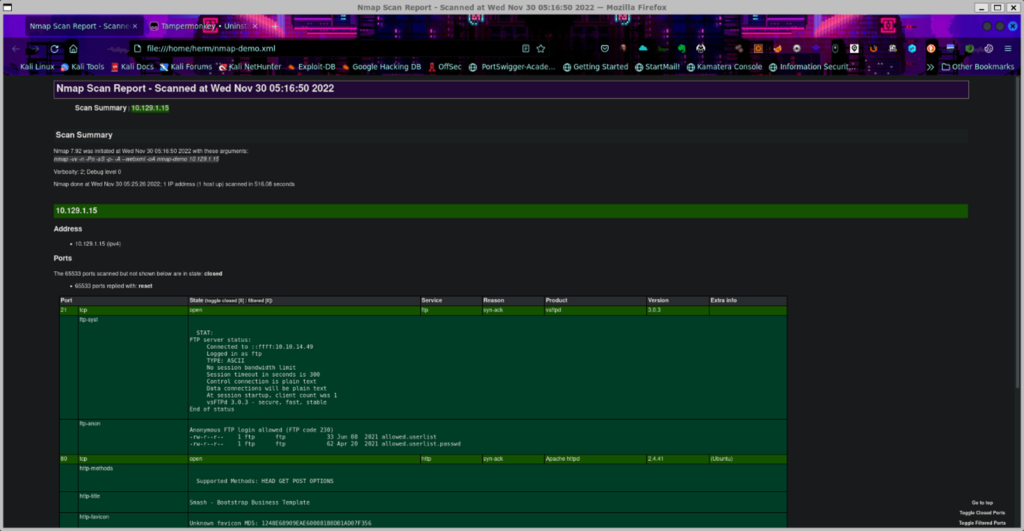
Figure 6: XML formatted output with the –xml flag.
The XML output, which you can also give on its own as -oX, allows you to read the results in a webpage with some slick formatting like that seen in Figure 6 above.
What it does is it uses an XSLT file to add styling to the XML. By default, that XSLT points to a specific, local file on the host you’re running Nmap from. This can be problematic and annoying, with multiple possible paths existing based on how you installed nmap.
But there’s good news. If you add –webxml to your command string it’ll produce an XML that has the web version of the XSLT, so it doesn’t matter how or where Nmap was installed!
Consider adding -oA and –webxml to your default nmap command line.