Cyber SecurityCase Study: How We Identified and Mitigated a Major Telerik UI Security Vulnerability
By: Herm Cardona
In the world of cybersecurity, threats can be unassuming, hidden in plain sight, and the Telerik UI for ASP.NET AJAX deserialization vulnerability is a prime example of such a threat. In this article, we will dive deep into how we identified and mitigated this major security vulnerability.
The Telerik UI is a popular suite of interface controls for ASP.NET applications. However, several versions (2007.1.621.20 to 2019.3.1023) of the suite contain a vulnerability that, if left unpatched, leaves applications open to attack. Figure 1 below shows the sectors most often targeted by this vulnerability.
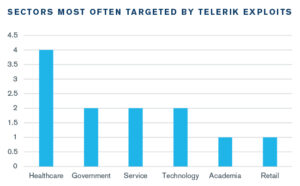
Figure 1: Sectors Targeted by Telerik Exploits
The Discovery
The Telerik deserialization vulnerability came to our attention during a routine penetration test of a client’s web application. We employed an array of tactics, one of which included using the Qualys WAS scanning tool to help us identify known vulnerabilities. The scanner flagged the Telerik vulnerability, indicating that an outdated and vulnerable version of the Telerik UI controls was in use.
Understanding the Vulnerability
The vulnerability lies in the RadAsyncUpload function, which is used to manage file uploads. When not correctly configured or when used in a default state, the function can permit arbitrary file uploads, leading to what is known as a Remote Code Execution (RCE) vulnerability. Essentially, this means an attacker can execute any code they wish on the server running the application.
The Mitigation Process
Once we identified the vulnerability, our first step was to confirm it. This was done using a proof-of-concept exploit to test the vulnerability, in a controlled and ethically guided manner. This confirmed the presence of the Telerik vulnerability and allowed us to demonstrate the risk to our client effectively.
Our immediate recommendation was to update the Telerik UI to the latest version, which has patched this vulnerability. However, in real-world scenarios, immediate updates aren’t always feasible due to potential disruptions in service or compatibility issues.
While planning for an update, we suggested implementing a few interim controls to mitigate the risk. These included:
- Restricting permissions: We ensured that the application’s server account had the least number of permissions necessary to function, reducing the potential impact of an attack.
- Monitoring traffic: By implementing an Intrusion Detection System (IDS) and setting up alerts for suspicious activities, we added an extra layer of security.
- Implementing a Web Application Firewall (WAF): A WAF configured with rules to block known exploitation attempts can serve as a temporary buffer against attacks.
Once the client had updated the Telerik UI controls to the most recent, secure version, we retested the application to ensure the vulnerability was patched effectively. Post this, we conducted another round of penetration testing to ensure no other vulnerabilities had been introduced during this process.
Reflections
The Telerik vulnerability served as a reminder that cybersecurity is not a set-it-and-forget-it endeavor. It’s an ongoing process that requires vigilance and an understanding that every part of a system, even those that seem insignificant, can become a potential attack vector.
Through proactive identification and timely action, we were able to prevent a possible cyber-attack, securing our client’s application.
Whether you’re a small business or a multinational corporation, vulnerabilities like this can lurk in your systems. Cybersecurity is an investment to protect your operations, your reputation, and, most importantly, your data.
Don’t become the next victim of a breach. Schedule your penetration test today, and let’s work together to secure your digital world.